Malware analysis
After finding a malware, there needs to be steps to analyze it by figuring out what type of malware it is, what it can do, and whether it is a […]

After finding a malware, there needs to be steps to analyze it by figuring out what type of malware it is, what it can do, and whether it is a […]
Statistical flow analysis is the method where we find anomalies in the flow of packet traffic by looking at the statistics of the data. This can include a sudden spike […]
This blog’s focuses on how to extract wireless data for use in network forensics. There are several common wireless devices: AM/FM radios cell phones Bluetooth headsets Wi-Fi (802.11) WiMax 802 […]
There are a different types of logs in a computer, for instance event logs and security logs. In order to see the event logs in Windows 10, search for ‘Event […]
Listed are different logs system that can be used and analyze for different environment and applications: OS Logs • Windows – Event Logs • Linux – Syslog • Application Logs […]
NIDS is Network-based Intrusion Detection System, the tools here are used to detect if there are anomalies or suspicious behavior in our personal network. It sees traffic flow in the […]
Switchers map mac addresses of all devices in network which then maps to the switch port, locate the physical location of MACs .It also consists of ARP table (Address Resolution […]
This class we learned about evidence acquisition. The best possible outcome is the perfect-fidelity evidence with no impact on network environment. However, it is not possible to achieve a zero […]
Malware means Malicious Software, a type of harmful computer a program that hackers used in order to gain access and sensitive information in one’s a computer. One of the way […]
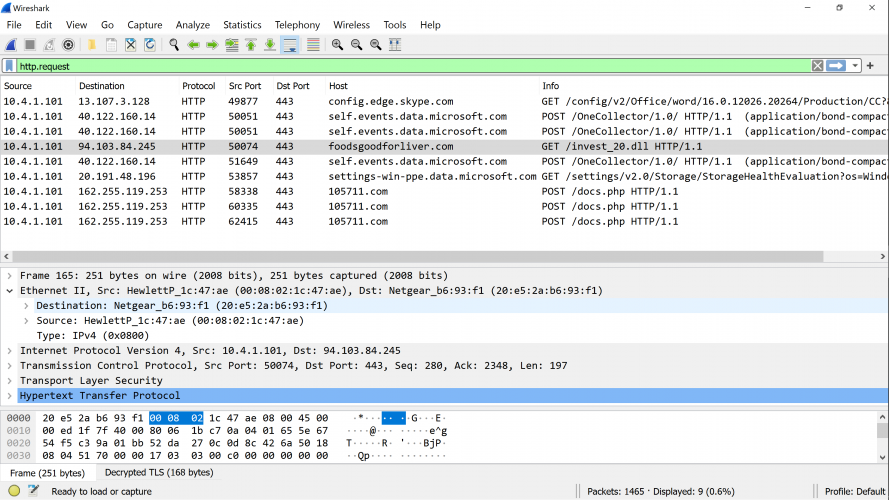
We learn some tools on dissecting evidences that have been gathered. Most of the time, the files that needs to be investigated is PCAP files. Tools such as Wireshark, tccpflor, […]