Disclaimer
This guide is solely for educational purposes only. Any acts of hacking taught here is for Ethical Hacking. Any hacking actions done without permission of owner is considered an illegal act by the law. Hence, do practice on your own network structure and your own devices.
SQL Injection is a very popular methods to attack web applications and websites in general. I will summarize the resource I found in https://www.guru99.com/learn-sql-injection-with-practical-example.html .
What is a SQL Injection?
SQL Injection is an attack that poisons dynamic SQL statements to comment out certain parts of the statement or appending a condition that will always be true.
How does it work?
Let’s say we have this query:
SELECT * FROM users WHERE email = ‘[userinput]’ AND password = md5(‘1234’);
The above code can be exploited by commenting out the password part and appending a condition that will always be true. Let’s suppose an attacker provides the following input in the email address field.
xxx@xxx.xxx’ OR 1 = 1 LIMIT 1 — ‘ ]
So, it will produce a final query like this:
SELECT * FROM users WHERE email = ‘xxx@xxx.xxx’ OR 1 = 1 LIMIT 1 — ‘ ] AND password = md5(‘1234’);
Explanation:
- xxx@xxx.xxx ends with a single quote which completes the string quote
- OR 1 = 1 LIMIT 1 is a condition that will always be true and limits the returned results to only one record.
- — ‘ AND … is a SQL comment that eliminates the password part.
You can try to go to http://www.techpanda.org to try this sql injection.
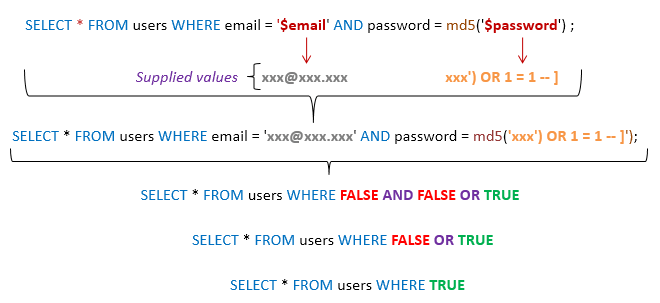
SELECT * FROM users WHERE email = ‘xxx@xxx.xxx’ AND password = md5(‘xxx’) OR 1 = 1 — ]’);
The process of how the query can produce a TRUE output as the result is shown in this picture below
Other SQL Injection attack types
SQL Injection can do more harm than just by passing the login algorithms. Some of the attacks include:
- Deleting data
- Updating data
- Inserting data
- Executing commands on the server that can download and install malicious programs such as Trojans
- Exporting valuable data such as credit card details, email, and passwords to the attacker’s remote server
- Getting user login details etc

